A Security Checklist
Contemporary Solutions to Growing Security Issues
Europe seems for the most part to be a blissful island of peace and harmony. Paying continuous attention to personal safety is not an issue for most of the European Union's 830 million inhabitants. But for how long will this situation prevail? It is thanks to the efforts of all the various security forces that things are so peaceful. Working away in the background, we don't notice the high-tech equipment that is being used to maintain this situation. This article turns our attention to some of the techniques and technology used to nip crime and terrorist threats in the bud.
Internal security is a contemporary subject to which the man in the street gives no special importance. Why would he when he can see no threat? It‘s a completely different situation in countries such as South Africa where private houses or hotels often resemble a small fortress. But a glance across the Atlantic gives cause for concern. Whole residential areas are fenced in and the access roads patrolled by security guards. Until now, it was only a question of how long it‘s going to be before that way of life becomes commonplace here too.
But when you take a closer look, you can see many countries - in particular outside Europe - where security plays a much more dominant role than it does here today. And because the threat is not perceived in our community, the readiness to invest in internal security or to accept compromises for personal safety is only very limited. This unfortunately does not mean, however, that security in Europe is a matter of course. If we want to ensure this security in the long term, we have no alternative but to do something about it.
Measures to Maintain and to Restore Security
There are two approaches to increasing security: on the one hand, to make the vulnerable ‚Achilles heel‘ more difficult to reach; on the other hand to obtain information in good time through intensive observation, which enables successful defense against a threat. Thirdly, the resources that are called upon when a disrupted environment has to be restored to a secure situation must be considered. The cause of the disturbance is immaterial: whether it was a terror attack or a natural catastrophe - in every case, basic supplies to the general public must be reinstated as quickly as possible.
Secure Communication
In the era of Twitter and Facebook - to name just two of the forums in the today‘s Internet - the handling of valuable information that should be protected is becoming even more difficult. This is not least because of the careless attitude of the media that quickly forgets potential danger. Central directions are called for here in government agencies and companies that ‚enforce‘ secure communication - for example using products from the Snapshield family. Nothing changes for the user in his normal behavior - but the background technology ensures that your information is encrypted before transmission and telephone calls cannot be followed. Both analog telephones and ISDN systems are supported, also Bluetooth mobiles or Blackberrys and iPhones.
The decision to adopt TETRA after a nurturing phase of over ten years has given the emergency and rescue services a universal digital communications system that is capable of speech encryption, has been introduced in the first towns during 2010 and will be generally available by 2012 - some speak of 2014. Unfortunately, this process, which began in 1996, has not only taken a long time but has remained with very old technology that today is neither ‚state-of-the-art‘ nor does it allow wideband data transmission. This means that the rapid transfer of situation images, videos of an accident location or the quick transmission of a phantom photo to a police car, to mention just a few applications, remain a dream. However, Telefunken Racoms can help here with various broadband ‚add-on‘ solutions that permit development from a simple emergency services network to a powerful ad hoc network.
Protection of Critical Infrastructure
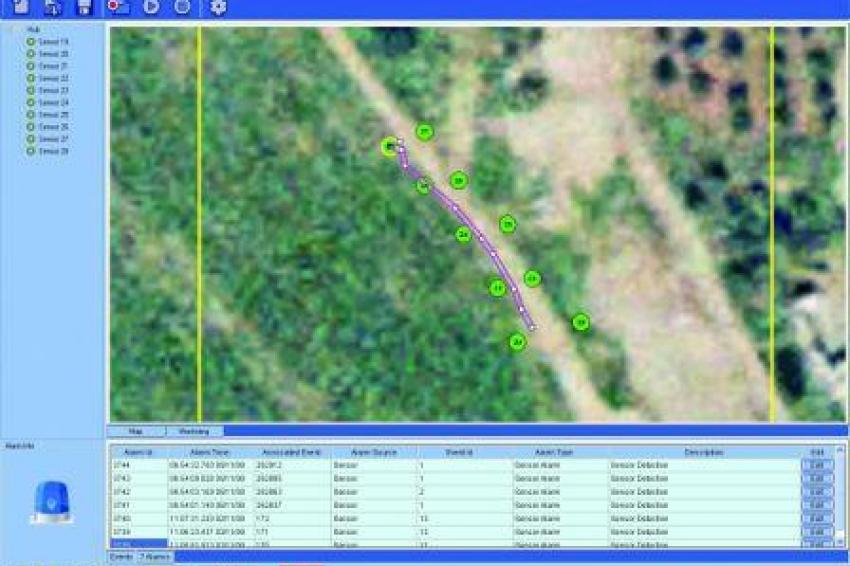
Whether a harbor or a nuclear power station, what they both have in common is that the availability of these resources is extremely important for our community. Apart from camera systems and sensors in fences, the compound can also be monitored for vibration. The seismic sensors developed for this task are connected to one another by radio. The battery life lies somewhere between five and ten years so that these systems are considered very easy to maintain. A system is available under the name ‚SAND‘ (Smart All-Terrain Networked Detectors) that detects vibrations and reports them to a central point that displays the alarms on a map.
Information from the Air - Have an Overview All the Time
The floods highlighted the situation, the international church congress also showed the gaps just as the European football championship did: often nobody had an overview of the situation! Operating helicopters is expensive, their constant availability is not guaranteed; the use of drones is only allowed in controlled airspace - and already the dilemma in which we regularly find ourselves during planned as well as short-notice events is clear. Here the TELESTAT can provide a solution. It is a system - part balloon, part kite - that is quickly available, with simple operator approval and low costs. Depending upon the area of application, the system can be fitted with various types of camera that transmit real-time video or high definition images to the ground station.
Turning Night into Day - See but Don‘t Be Seen
Although heat-sensitive cameras were once the tool of choice to be able to gain information at night in total darkness, this technology has its limits. On the one hand - as the name suggests - only sources of heat can be shown. Every other detail (writing, number plates, people behind glass, for example sitting in a car) remained out of sight - but not however when LIGHT technology is used. Where the coastguard is on duty, objects can be identified at up to eight kilometers distance. This novel laser-supported system doesn‘t only have excellent optics; the built-in electronic stabilizer guarantees a stable image and the functional principle also permits vision through fog, rain, snow or smoke, without affecting the image of the observed object.
The mobile version can be used up to a distance of 500 meters. As the same technology is used, the system‘s characteristics are also the same: no blurring from heat sources in front of the observed objects, viewing through glass (window panes, car windscreens, cockpit canopies), no disturbance through rain, snow, fog or smoke.
Training for the Emergency
Luckily emergencies caused by natural catastrophes or terrorist activity are rare today. And the question of training and education goes along with this line of thinking. What must be done and when? Will the team leaders make the right decision at the right moment? Do things happen in practice just as they were imagined in theory? Answers to these questions can be provided by the HLS² Training Center - a Homeland Security Simulation for the training of crisis managers. With the help of realistic scenarios, the events are simulated in real time, the reactions of the decision-makers recorded and analyzed afterwards so that the next emergency situation doesn‘t catch us by surprise and swamp us.
Contact
Telefunken Radio Communication Systems GmbH & Co.KG
Eberhard-Finckh-Str. 55
89075 Ulm
Germany
+49 731 1553 0
+49 731 1553 112