Five Risk Factors with Overnight Deliveries
01.03.2023 - Deliveries at night are often conducted by logistics companies and third-party providers, whose drivers must have access to the building, storage or cold rooms outside of business hours. With service providers and drivers changing more and more frequently, the risk is no longer tenable for most business owners or decision-makers.
According to current studies, a higher security level is the main reason why property owners equip their buildings with intelligent SmartHome or access control systems.* One area of application in which the advantages are particularly evident are the so-called “dark deliveries”.
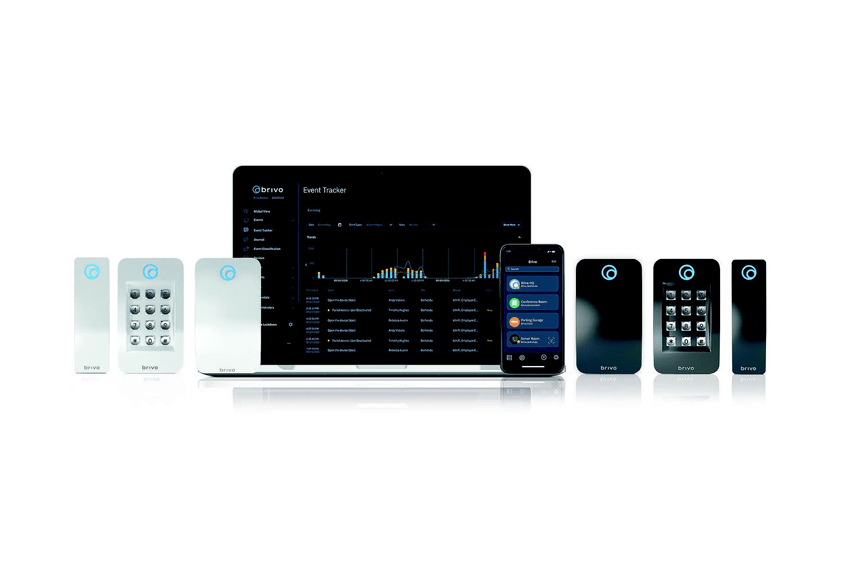
In many organizations – especially restaurants, canteens and grocery stores – goods are often delivered overnight, outside of business hours. On the one hand, ongoing operations are less disrupted, and on the other hand, products with a very short shelf life, such as seafood, herbs, baked goods or convenience food, are freshly available in the morning. One problem, however, is the access control for the suppliers and changing drivers. Access Management expert Brivo explains the risks and challenges associated with overnight deliveries, showing why digital solutions like mobile credentials are becoming more prevalent. Such solutions enable managers to assign specific access rights to employees and external partners, which can then for example authenticate themselves via their smartphone and use it as a key to access buildings or certain areas.
Overnight deliveries are often conducted by logistics companies and third-party providers, whose drivers must have access to the building, storage or cold rooms outside of business hours. In the past, this was often handled with a high degree of trust. With service providers and drivers changing more and more frequently, the risk is no longer tenable for most business owners or decision-makers.
Missing Backup and Communication Gaps With the “Gatekeeper Method”
One method of admitting access to suppliers is for an employee or security guard to be present, even late at night or early in the morning, to verify the identity of the suppliers and to open any necessary doors to the building and store or cold rooms. However, this procedure harbors more possible sources of error than assumed at first glance. If an internal employee is assigned to access control, there is often no backup. If the person gets sick or can’t turn up, sometimes a manager has to travel a long way in the middle of the night to ensure that several kilograms of seafood are not left standing in front of a locked door – if the absence of the person appointed is recognized at all. If there is a security service responsible for the building, then they must be able to verify the suppliers and drivers. Here, there are often breaks in communication, because the staff on the side of the suppliers and logistics services as well as the security service changes frequently.
Trust Risk in the “Key Strategy”
In the past, business owners often simply provided a trusted supplier with a key. What is perhaps still feasible for a restaurant owner with 1-2 suppliers cannot really be implemented in larger companies with changing delivery services and drivers. This approach not only requires a high level of trust in the logistics partner. The key must also be passed back and forth between people if the same person does not always take over the delivery. If a key is lost, there are also high costs for replacing the entire locking system. Of course, this not only applies to the suppliers, but also in the event of an employee losing a key.
High Effort With Token Solutions
A first step towards digital solutions to replace keys are locks with number combinations or tokens that are programmed. However, when access codes change, all employees and suppliers must be reliably informed, and there is no control over who may pass their code on to third parties. The problem is similar for tokens. While it is more difficult to pass a card or token along than a number code, the cost of the system and the amount of programming work are much higher.
Lack of Control Over Time Slots for Access
When keys, codes or tokens are issued, there is usually no way of specifying a precise window of time for a specific delivery. In the case of tokens, this could be implemented with a certain amount of effort – but if, for example, there is a delay in delivery, someone from the IT or security team who could adjust the time window is not always available at that time. Overall, there is a high risk factor for all these options, as in most cases, it cannot be regulated or supervised at what times and for what purpose employees and external partners use their access to the building or certain rooms.
Lack of Transparency About Deliveries Conducted
Another shortcoming with many of the previously described methods is that those responsible cannot remotely check whether a delivery has arrived and whether the goods have been properly stored – for example in a cooler. If the missing delivery or improper handling is noticed, the goods may already be unusable or cannot be replaced in time. For a large staff restaurant, catering for an important event or delivery to a large fast food or supermarket chain, such a failure can result in enormous costs.
“Many larger companies have already implemented stronger security measures. So far, however, this was often associated with high costs and considerable effort,” explains Ingo Meijer, VP of EMEA, at Brivo. “A large restaurant chain, for example, turned to us because it took an average of 30 minutes to register a driver for the access system and equip him with the necessary token. However, since the drivers change more and more frequently, the previous system was no longer practicable. For this reason, they decided to switch to a mobile credential access system.”
A modern system for mobile access control offers the advantage that no dedicated hardware is required. Access authorization and authentication can be implemented via the smartphones of employees or suppliers. If the owner has the necessary access rights, the smartphone serves as a kind of key for access to buildings or specially secured areas. A mobile app communicates with the reader at the door and allows users to access premises – without the traditional plastic cards, tokens, etc. that have to be handed over and programmed. Access rights can be assigned and adjusted in real time via the cloud without the need for an internal IT team. Mobile credential systems thus provide the basis for a holistic and integrated access control system that increases both security and convenience for employees and external partners.
* https://www.bitkom.org/Presse/Presseinformation/Smart-Home-2022
Contact
Brivo Systems LLC
4330 E.W.Highway,Suite 250
Bethesda,Maryland 20814
United States
+1 514 907 19289